-->
Login to your Malwarebytes account to manage subscriptions (including upgrades and renewals), payments, and devices. You can also view orders and find quick links to support.
Malware is the overarching name for applications and other code, like software, that Microsoft classifies more granularly as malicious software or unwanted software. Malicious software In general, malicious software wants to trick, cheat, or defrauds users, placing them in vulnerable states. When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen. Click on the Get started button. Click Scan to start a Threat Scan. Click Quarantine to remove the found threats. Reboot the system if prompted to complete the removal process. Malwarebytes 4.3.0.216 on 32-bit and 64-bit PCs. This download is licensed as freeware for the Windows (32-bit and 64-bit) operating system on a laptop or desktop PC from antivirus without restrictions. Malwarebytes Anti-Malware 4.3.0.216 is available to all software users as a free download for Windows. With the world-leading Bitdefender antivirus engine, IObit Anti-malware engine, and Anti-ransomware Engine, IObit Malware Fighter 8 can remove the latest spyware, adware, ransomware, Trojans, keyloggers, bots, worms, hijackers, and viruses, etc. Additionally, IObit Malware Fighter 8 can also ensure a more secure browser and system with six.
Microsoft aims to provide a delightful and productive Windows experience by working to ensure you're safe and in control of your devices. Microsoft helps protect you from potential threats by identifying and analyzing software and online content. When you download, install, and run software, we check the reputation of downloaded programs and ensure you're protected against known threats. You are also warned about software that is unknown to us.
You can assist Microsoft by submitting unknown or suspicious software for analysis. This will help ensure that unknown or suspicious software is scanned by our system to start establishing reputation. Learn more about submitting files for analysis
The next sections provide an overview of the classifications we use for applications and the types of behaviors that lead to that classification.
Note
New forms of malware and potentially unwanted applications are being developed and distributed rapidly. The following list may not be comprehensive, and Microsoft reserves the right to adjust, expand, and update these without prior notice or announcement.
Unknown – Unrecognized software
No antivirus or protection technology is perfect. It takes time to identify and block malicious sites and applications, or trust newly released programs and certificates. With almost 2 billion websites on the internet and software continuously updated and released, it's impossible to have information about every single site and program.

Think of Unknown/Uncommonly downloaded warnings as an early warning system for potentially undetected malware. There's generally a delay from the time new malware is released until it's identified. Not all uncommon programs are malicious, but the risk in the unknown category is much higher for the typical user. Warnings for unknown software aren't blocks. Users can choose to download and run the application normally if they wish to.
Once enough data is gathered, Microsoft's security solutions can make a determination. Either no threats are found, or an application or software is categorized as malware or potentially unwanted software.
Malware
Malware is the overarching name for applications and other code, like software, that Microsoft classifies more granularly as malicious software or unwanted software.
Malicious software
Malicious software is an application or code that compromises user security. Malicious software may steal your personal information, lock your device until you pay a ransom, use your device to send spam, or download other malicious software. In general, malicious software wants to trick, cheat, or defrauds users, placing them in vulnerable states.
Microsoft classifies most malicious software into one of the following categories:
Backdoor: A type of malware that gives malicious hackers remote access to and control of your device.
Downloader: A type of malware that downloads other malware onto your device. It must connect to the internet to download files.
Dropper: A type of malware that installs other malware files onto your device. Unlike a downloader, a dropper doesn't have to connect to the internet to drop malicious files. The dropped files are typically embedded in the dropper itself.
Exploit: A piece of code that uses software vulnerabilities to gain access to your device and perform other tasks, such as installing malware. See more information about exploits.
Hacktool: A type of tool that can be used to gain unauthorized access to your device.
Macro virus: A type of malware that spreads through infected documents, such as Microsoft Word or Excel documents. The virus is run when you open an infected document.
Obfuscator: A type of malware that hides its code and purpose, making it more difficult for security software to detect or remove.
Password stealer: A type of malware that gathers your personal information, such as usernames and passwords. It often works along with a keylogger, which collects and sends information about the keys you press and websites you visit.
Ransomware: A type of malware that encrypts your files or makes other modifications that can prevent you from using your device. It then displays a ransom note that states you must pay money or perform other actions before you can use your device again. See more information about ransomware.
Rogue security software: Malware that pretends to be security software but doesn't provide any protection. This type of malware usually displays alerts about nonexistent threats on your device. It also tries to convince you to pay for its services.
Trojan: A type of malware that attempts to appear harmless. Unlike a virus or a worm, a trojan doesn't spread by itself. Instead, it tries to look legitimate to tricks users into downloading and installing it. Once installed, trojans perform various malicious activities such as stealing personal information, downloading other malware, or giving attackers access to your device.
Trojan clicker: A type of trojan that automatically clicks buttons or similar controls on websites or applications. Attackers can use this trojan to click on online advertisements. These clicks can skew online polls or other tracking systems and can even install applications on your device.
Worm: A type of malware that spreads to other devices. Worms can spread through email, instant messaging, file sharing platforms, social networks, network shares, and removable drives. Sophisticated worms take advantage of software vulnerabilities to propagate.
Unwanted software
Microsoft believes that you should have control over your Windows experience. Software running on Windows should keep you in control of your device through informed choices and accessible controls. Microsoft identifies software behaviors that ensure you stay in control. We classify software that doesn't fully demonstrate these behaviors as 'unwanted software'.
Lack of choice
You must be notified about what is happening on your device, including what software does and whether it's active.
Software that exhibits lack of choice might:
Fail to provide prominent notice about the behavior of the software and its purpose and intent.
Fail to clearly indicate when the software is active. It might also attempt to hide or disguise its presence.
Install, reinstall, or remove software without your permission, interaction, or consent.
Install other software without a clear indication of its relationship to the primary software.
Circumvent user consent dialogs from the browser or operating system.
Falsely claim to be software from Microsoft.
Software must not mislead or coerce you into making decisions about your device. It is considered behavior that limits your choices. In addition to the previous list, software that exhibits lack of choice might:
Display exaggerated claims about your device's health.
Make misleading or inaccurate claims about files, registry entries, or other items on your device.
Display claims in an alarming manner about your device's health and require payment or certain actions in exchange for fixing the purported issues.

Software that stores or transmits your activities or data must:
- Give you notice and get consent to do so. Software shouldn't include an option that configures it to hide activities associated with storing or transmitting your data.
Lack of control
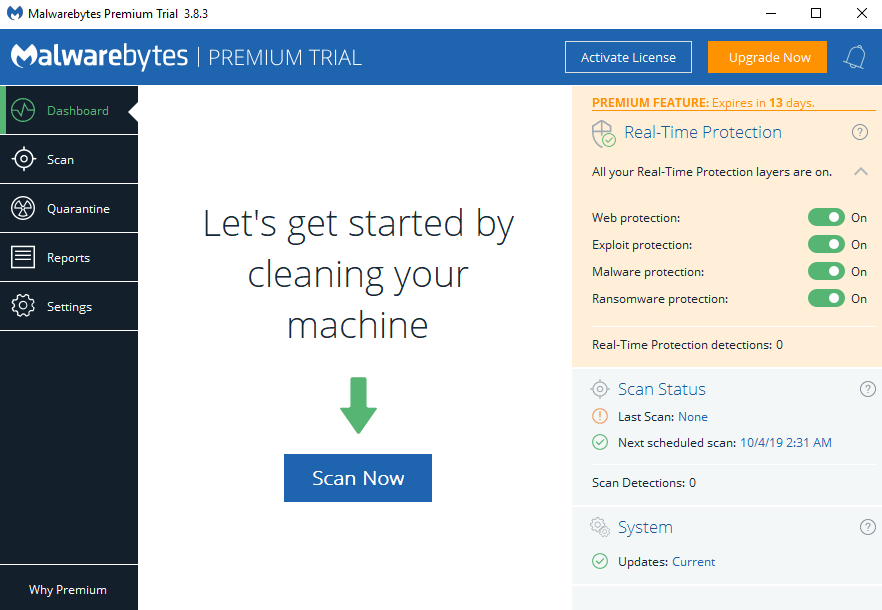
You must be able to control software on your device. You must be able to start, stop, or otherwise revoke authorization to software.
Software that exhibits lack of control might:
Prevent or limit you from viewing or modifying browser features or settings.
Open browser windows without authorization.
Redirect web traffic without giving notice and getting consent.
Modify or manipulate webpage content without your consent.
Software that changes your browsing experience must only use the browser's supported extensibility model for installation, execution, disabling, or removal. Browsers that don't provide supported extensibility models are considered non-extensible and shouldn't be modified.
Installation and removal
You must be able to start, stop, or otherwise revoke authorization given to software. Software should obtain your consent before installing, and it must provide a clear and straightforward way for you to install, uninstall, or disable it.
Malwarebytes Free 30 Day Trial
Software that delivers poor installation experience might bundle or download other 'unwanted software' as classified by Microsoft.
Software that delivers poor removal experience might:
Malware Bitcoin Threat
Present confusing or misleading prompts or pop-ups when you try to uninstall it.
Fail to use standard install/uninstall features, such as Add/Remove Programs.
Advertising and advertisements
Software that promotes a product or service outside of the software itself can interfere with your computing experience. You should have clear choice and control when installing software that presents advertisements.
The advertisements that are presented by software must:
Include an obvious way for users to close the advertisement. The act of closing the advertisement must not open another advertisement.
Include the name of the software that presented the advertisement.
The software that presents these advertisements must:
- Provide a standard uninstall method for the software using the same name as shown in the advertisement it presents.
Advertisements shown to you must:
Be distinguishable from website content.
Not mislead, deceive, or confuse.
Not contain malicious code.
Not invoke a file download.
Consumer opinion
Microsoft maintains a worldwide network of analysts and intelligence systems where you can submit software for analysis. Your participation helps Microsoft identify new malware quickly. After analysis, Microsoft creates Security intelligence for software that meets the described criteria. This Security intelligence identifies the software as malware and are available to all users through Microsoft Defender Antivirus and other Microsoft antimalware solutions.
Potentially unwanted application (PUA)
Our PUA protection aims to safeguard user productivity and ensure enjoyable Windows experiences. This protection helps deliver more productive, performant, and delightful Windows experiences. For instruction on how to enable PUA protection in Chromium-based Microsoft Edge and Microsoft Defender Antivirus, see Detect and block potentially unwanted applications.
PUAs are not considered malware.
Microsoft uses specific categories and the category definitions to classify software as a PUA.
Advertising software: Software that displays advertisements or promotions, or prompts you to complete surveys for other products or services in software other than itself. This includes software that inserts advertisements to webpages.
Torrent software (Enterprise only): Software that is used to create or download torrents or other files specifically used with peer-to-peer file-sharing technologies.
Cryptomining software: Software that uses your device resources to mine cryptocurrencies.
Bundling software: Software that offers to install other software that is not developed by the same entity or not required for the software to run. Also, software that offers to install other software that qualifies as PUA based on the criteria outlined in this document.
Marketing software: Software that monitors and transmits the activities of users to applications or services other than itself for marketing research.
Evasion software: Software that actively tries to evade detection by security products, including software that behaves differently in the presence of security products.
Poor industry reputation: Software that trusted security providers detect with their security products. The security industry is dedicated to protecting customers and improving their experiences. Microsoft and other organizations in the security industry continuously exchange knowledge about files we have analyzed to provide users with the best possible protection.
Malwarebytes Anti Malware Premium Full Crack Download. What is Malwarebytes Anti Malware Premium? This application is an anti-malware or antivirus software specifically designed to clean up and anticipate Malware Viruses on your PC. This application has been developed exclusively as a solution to detect a variety of malicious software coming to your computer. As you might have known, Malwarebytes Anti Malware Premium can detect and remove malware that even the most well-known anti-virus and anti-malware applications on the market today cannot handle.
It works by monitoring each process and stopping the process that is likely to damage your PC. In other words, even before the malicious program starts to react, this software would kill them immediately. On top of that, Malware can completely remove any kind of adwares, it also has Malicious websites blocker with a single click. Above all that, Malwarebytes Premium has quite achivements from various label around the world for its performance.

To get the latest Malwarebytes Premium Download link for free, you can do it easily from the panel below. However, before you start installing this application, you need to understand about using keygen first. Therefore, your application can run without any problem with its full features. Do you want to try this software before buying it officially? Get Malwarebytes Premium free. download full Version with the newest keygen.
Malwarebytes Premium 4.2 Full Setup Details
- Software Full Name : Malwarebytes Premium 4.2 Full Version.
- Setup File Name : mlp420prm.rar & mlm420crsx.rar.
- Full Setup Size : 190 MB.
- Setup Type : Offline Installer with Patch.
- Compatibility Architecture : 32 Bit & 64 Bit.
- Latest Release Added On : January 28th, 2021.
Malwarebytes Premium Anti Malware Features

Think of Unknown/Uncommonly downloaded warnings as an early warning system for potentially undetected malware. There's generally a delay from the time new malware is released until it's identified. Not all uncommon programs are malicious, but the risk in the unknown category is much higher for the typical user. Warnings for unknown software aren't blocks. Users can choose to download and run the application normally if they wish to.
Once enough data is gathered, Microsoft's security solutions can make a determination. Either no threats are found, or an application or software is categorized as malware or potentially unwanted software.
Malware
Malware is the overarching name for applications and other code, like software, that Microsoft classifies more granularly as malicious software or unwanted software.
Malicious software
Malicious software is an application or code that compromises user security. Malicious software may steal your personal information, lock your device until you pay a ransom, use your device to send spam, or download other malicious software. In general, malicious software wants to trick, cheat, or defrauds users, placing them in vulnerable states.
Microsoft classifies most malicious software into one of the following categories:
Backdoor: A type of malware that gives malicious hackers remote access to and control of your device.
Downloader: A type of malware that downloads other malware onto your device. It must connect to the internet to download files.
Dropper: A type of malware that installs other malware files onto your device. Unlike a downloader, a dropper doesn't have to connect to the internet to drop malicious files. The dropped files are typically embedded in the dropper itself.
Exploit: A piece of code that uses software vulnerabilities to gain access to your device and perform other tasks, such as installing malware. See more information about exploits.
Hacktool: A type of tool that can be used to gain unauthorized access to your device.
Macro virus: A type of malware that spreads through infected documents, such as Microsoft Word or Excel documents. The virus is run when you open an infected document.
Obfuscator: A type of malware that hides its code and purpose, making it more difficult for security software to detect or remove.
Password stealer: A type of malware that gathers your personal information, such as usernames and passwords. It often works along with a keylogger, which collects and sends information about the keys you press and websites you visit.
Ransomware: A type of malware that encrypts your files or makes other modifications that can prevent you from using your device. It then displays a ransom note that states you must pay money or perform other actions before you can use your device again. See more information about ransomware.
Rogue security software: Malware that pretends to be security software but doesn't provide any protection. This type of malware usually displays alerts about nonexistent threats on your device. It also tries to convince you to pay for its services.
Trojan: A type of malware that attempts to appear harmless. Unlike a virus or a worm, a trojan doesn't spread by itself. Instead, it tries to look legitimate to tricks users into downloading and installing it. Once installed, trojans perform various malicious activities such as stealing personal information, downloading other malware, or giving attackers access to your device.
Trojan clicker: A type of trojan that automatically clicks buttons or similar controls on websites or applications. Attackers can use this trojan to click on online advertisements. These clicks can skew online polls or other tracking systems and can even install applications on your device.
Worm: A type of malware that spreads to other devices. Worms can spread through email, instant messaging, file sharing platforms, social networks, network shares, and removable drives. Sophisticated worms take advantage of software vulnerabilities to propagate.
Unwanted software
Microsoft believes that you should have control over your Windows experience. Software running on Windows should keep you in control of your device through informed choices and accessible controls. Microsoft identifies software behaviors that ensure you stay in control. We classify software that doesn't fully demonstrate these behaviors as 'unwanted software'.
Lack of choice
You must be notified about what is happening on your device, including what software does and whether it's active.
Software that exhibits lack of choice might:
Fail to provide prominent notice about the behavior of the software and its purpose and intent.
Fail to clearly indicate when the software is active. It might also attempt to hide or disguise its presence.
Install, reinstall, or remove software without your permission, interaction, or consent.
Install other software without a clear indication of its relationship to the primary software.
Circumvent user consent dialogs from the browser or operating system.
Falsely claim to be software from Microsoft.
Software must not mislead or coerce you into making decisions about your device. It is considered behavior that limits your choices. In addition to the previous list, software that exhibits lack of choice might:
Display exaggerated claims about your device's health.
Make misleading or inaccurate claims about files, registry entries, or other items on your device.
Display claims in an alarming manner about your device's health and require payment or certain actions in exchange for fixing the purported issues.
Software that stores or transmits your activities or data must:
- Give you notice and get consent to do so. Software shouldn't include an option that configures it to hide activities associated with storing or transmitting your data.
Lack of control
You must be able to control software on your device. You must be able to start, stop, or otherwise revoke authorization to software.
Software that exhibits lack of control might:
Prevent or limit you from viewing or modifying browser features or settings.
Open browser windows without authorization.
Redirect web traffic without giving notice and getting consent.
Modify or manipulate webpage content without your consent.
Software that changes your browsing experience must only use the browser's supported extensibility model for installation, execution, disabling, or removal. Browsers that don't provide supported extensibility models are considered non-extensible and shouldn't be modified.
Installation and removal
You must be able to start, stop, or otherwise revoke authorization given to software. Software should obtain your consent before installing, and it must provide a clear and straightforward way for you to install, uninstall, or disable it.
Malwarebytes Free 30 Day Trial
Software that delivers poor installation experience might bundle or download other 'unwanted software' as classified by Microsoft.
Software that delivers poor removal experience might:
Malware Bitcoin Threat
Present confusing or misleading prompts or pop-ups when you try to uninstall it.
Fail to use standard install/uninstall features, such as Add/Remove Programs.
Advertising and advertisements
Software that promotes a product or service outside of the software itself can interfere with your computing experience. You should have clear choice and control when installing software that presents advertisements.
The advertisements that are presented by software must:
Include an obvious way for users to close the advertisement. The act of closing the advertisement must not open another advertisement.
Include the name of the software that presented the advertisement.
The software that presents these advertisements must:
- Provide a standard uninstall method for the software using the same name as shown in the advertisement it presents.
Advertisements shown to you must:
Be distinguishable from website content.
Not mislead, deceive, or confuse.
Not contain malicious code.
Not invoke a file download.
Consumer opinion
Microsoft maintains a worldwide network of analysts and intelligence systems where you can submit software for analysis. Your participation helps Microsoft identify new malware quickly. After analysis, Microsoft creates Security intelligence for software that meets the described criteria. This Security intelligence identifies the software as malware and are available to all users through Microsoft Defender Antivirus and other Microsoft antimalware solutions.
Potentially unwanted application (PUA)
Our PUA protection aims to safeguard user productivity and ensure enjoyable Windows experiences. This protection helps deliver more productive, performant, and delightful Windows experiences. For instruction on how to enable PUA protection in Chromium-based Microsoft Edge and Microsoft Defender Antivirus, see Detect and block potentially unwanted applications.
PUAs are not considered malware.
Microsoft uses specific categories and the category definitions to classify software as a PUA.
Advertising software: Software that displays advertisements or promotions, or prompts you to complete surveys for other products or services in software other than itself. This includes software that inserts advertisements to webpages.
Torrent software (Enterprise only): Software that is used to create or download torrents or other files specifically used with peer-to-peer file-sharing technologies.
Cryptomining software: Software that uses your device resources to mine cryptocurrencies.
Bundling software: Software that offers to install other software that is not developed by the same entity or not required for the software to run. Also, software that offers to install other software that qualifies as PUA based on the criteria outlined in this document.
Marketing software: Software that monitors and transmits the activities of users to applications or services other than itself for marketing research.
Evasion software: Software that actively tries to evade detection by security products, including software that behaves differently in the presence of security products.
Poor industry reputation: Software that trusted security providers detect with their security products. The security industry is dedicated to protecting customers and improving their experiences. Microsoft and other organizations in the security industry continuously exchange knowledge about files we have analyzed to provide users with the best possible protection.
Malwarebytes Anti Malware Premium Full Crack Download. What is Malwarebytes Anti Malware Premium? This application is an anti-malware or antivirus software specifically designed to clean up and anticipate Malware Viruses on your PC. This application has been developed exclusively as a solution to detect a variety of malicious software coming to your computer. As you might have known, Malwarebytes Anti Malware Premium can detect and remove malware that even the most well-known anti-virus and anti-malware applications on the market today cannot handle.
It works by monitoring each process and stopping the process that is likely to damage your PC. In other words, even before the malicious program starts to react, this software would kill them immediately. On top of that, Malware can completely remove any kind of adwares, it also has Malicious websites blocker with a single click. Above all that, Malwarebytes Premium has quite achivements from various label around the world for its performance.
To get the latest Malwarebytes Premium Download link for free, you can do it easily from the panel below. However, before you start installing this application, you need to understand about using keygen first. Therefore, your application can run without any problem with its full features. Do you want to try this software before buying it officially? Get Malwarebytes Premium free. download full Version with the newest keygen.
Malwarebytes Premium 4.2 Full Setup Details
- Software Full Name : Malwarebytes Premium 4.2 Full Version.
- Setup File Name : mlp420prm.rar & mlm420crsx.rar.
- Full Setup Size : 190 MB.
- Setup Type : Offline Installer with Patch.
- Compatibility Architecture : 32 Bit & 64 Bit.
- Latest Release Added On : January 28th, 2021.
Malwarebytes Premium Anti Malware Features
- Light speed quick scanning Anti Virus.
- Ability to perform full scans for all drives.
- Malwarebytes anti malware Protection Module. (requires registration).
- Antivirus Database updates released daily.
- Quarantine to hold threats and restore them at your convenience.
- Ignore list for both the scanner and Protection Module.
- Free ware Settings to enhance your anti malware performance.
- A small list of extra utilities to help remove malware manually.
- Multi-lingual support and also it works together with other anti malware utilities.
- Command line support for anti virus quick scanning.
- Context menu integration to scan files on demand.
- Malwarebytes Premium download link with keygen.
- Support Windows 10 Redstone 64 bit and 32 bit.
- Support Windows 7 ultimate SP1.
- Also support Windows 8.1 the latest update.
How to Install Malwarebytes Premium Full Version
- You must uninstall the previous version of Malwarebytes!
- Download Malwarebytes Full Version.
- Turn off Antivirus and Windows Defender.
- Extract files with Winrar 5.6.
- Follow the how to instruction to crack the software.
- Install Malwarebytes, run the application.
- Enjoy bro!
Alternative Software :Gridinsoft Anti Malware Full Crack
Download Malwarebytes Premium Full Crack
Installer Windows | FileUpload | ZippyShare | 182 MB
Keygen Only | ZippyShare | FileUpload | 1 MB
Password : www.yasir252.com

